Amidst the ongoing Russo-Ukrainian war, nations, institutions, and individuals providing aid to Ukraine have faced relentless cyberattacks by pro-Russian hackers.
NoName057(16), a pro-Russian hacking entity, made its presence known in March 2022 and has often been at the forefront of several such cyber attacks, claiming responsibility for targeting an array of governmental agencies, media outlets, and private corporations.
These attacks, spanned Ukrainian, American, and European targets, have escalated tensions within the current cybersecurity landscape, prompting cybersecurity experts to look further.
Interestingly, the activities of NoName057(16) were being closely monitored by researchers at Radware, who went undercover as hacktivists to find out more about the workings of the NoName hacktivist group.

NoName057(16) operations include the work of thousands of volunteers and the main members who handle cyber attacks in tandem. Moreover, the group engaged in a distinctive method of recruitment, compensating volunteers in a specific manner.
The Cyber Express conversed with the security researcher revealed information about NoName057(16); From divulging the group’s daily budget allocated for their unsettling payments to unearthing their cryptic CryptoBot tokens, the conversation highlighted the mechanisms fueling this digital insurgency.
Q1. Can you provide an overview of NoName057(16)’s organizational structure? How centralized is their decision-making, and what insight did you gather regarding the leadership and roles within the group as undercover hacktivists?
We do not have evidence of the structure or the number of core members in the group. No one has stepped up as the declared leader of NoName057(16), unlike Killnet where Killmilk is the recognized leader and mastermind behind the group.
We assume NoName057(16) has a horizontal structure and is composed of a handful of core members who do the following –
- Operate the Telegram channel
- Code the DDoSia bot
- Maintain the DDoSia infrastructure
- Do the osint research to find new targets
- Research targets to optimize attack vectors
- Support the community of volunteers that run the group’s bot.
NoName057(16) operates several communication channels. The group communicates in Russian through its main Telegram channel (https://t.me/noname05716). In August 2022, they created a second channel (https://t.me/noname05716eng), which provides an English translation of the messages from the main channel.
We assume they created this English channel to carry their message outside the Russian-speaking community, primarily to get the attention of the media, researchers, and potential victims. They also own a Telegram group called ‘DDoSia Project’ to provide instructions and support for Russian- and English-speaking volunteers running their bot.
In addition, they host a Telegram bot (https://t.me/DDosiabot, @DDosiabot) that provides a registration service and leaderboards for the volunteers. The DDoSia client bot is hosted as a ZIP file in the DDoSia Project group chat and can be downloaded from there.
Q2. With such a sizable community of over 10,000 members, how are NoName057(16) operations managed to maintain cohesion and effectiveness? Are there specific hierarchies or internal communications platforms beyond Telegram that they use?
The core group that makes up NoName057(16) is rather limited in size in our opinion. Most of the +10k members on the DDoSia Project and +50k members on NoName057(16) are volunteers and passive members. The volunteers provide resources for the DDoSia botnet.
The members of the main channel provide NoName057(16) visibility and influence.
Q3. Beyond the obvious political alignment with Russia, what are the primary motivations driving NoName057(16) operations? Did your undercover research indicate any financial, ideological, or personal reasons driving members, especially those at the helm?
NoName057(16) is purely patriotic and politically driven. They do not want to be associated with the pro-Russian hacktivist group Killnet (see https://t.me/noname05716/934 and the image below). They also never cooperate with Killnet.
Even though NoName057(16)’s and Killnet’s objectives are politically aligned with Russia and their targets have overlapped on some occasions in 2022, NoName057(16) has never officially joined a Killnet campaign or leveraged the Killnet badge.
Killnet has not performed many DDoS attacks in 2023. However, on many occasions, Killnet has reposted attacks claimed by NoName057(16), repurposing and consolidating several check-host.net links in new messages without attributing the attacks to NoName057(16).
Each check-host link has a unique ID, so older attacks that are reposted or repurposed can be easily tracked.
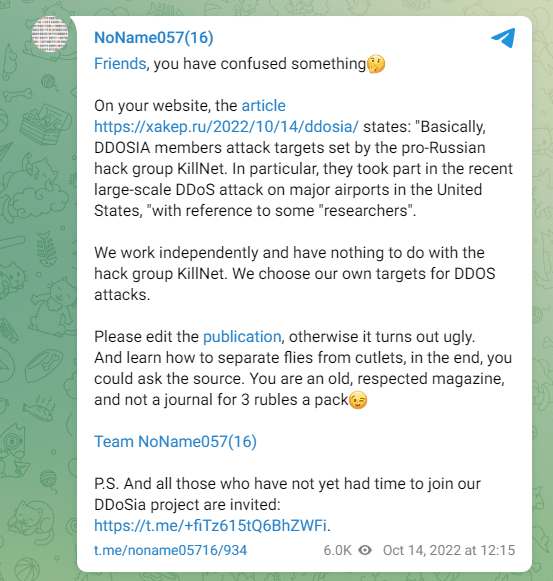
There are some exceptions to NoName057(16)’s political agenda. For example, in Oct 2022, a Russian reporter for hacker magazine ‘xakep.ru’ was threatened by the group when she wrote NoName057(16) was associated with Killnet.
NoName057(16) wanted this statement removed from the article and stated explicitly they did not want to be associated with Killnet!
Q.4 We’ve seen many DDoS groups with varying targets. In the case of NoName057(16), is there a particular pattern or criteria in selecting their targets? Additionally, how has their DDoS technique evolved over time?
NoName057(16) is very concise in its targeting and attack preparations. They typically target Western governments and pro-Ukrainian organizations based on statements or events covered in the media and any comments or actions that might negatively reflect on or impact Russia.

They rarely divert from their pattern and are concise in their messaging, almost always providing a reason for the attack.
Q.5 Could you delve deeper into the mechanics of the “DDoSia Project”? How does it differentiate from traditional DDoS botnets, and how does the integration of @CryptoBot and @DDosiabot on Telegram streamline their operations?
IoT DDoS botnets consist of compromised IoT devices. The device owners are not aware their devices have been abused for illegal activities.
To bootstrap an IoT botnet, the bot herders must scan the internet for vulnerable devices. Unless they use some IoT search engine such as shodan.io, zoomeye or censys to target their infection attempts, the bot herders will perform random and widespread internet scans while leveraging known vulnerabilities.
It is only a matter of time before such actions trip over a honeypot and the botnet infrastructure and the campaign are taken down or exposed by threat researchers monitoring such malicious activity.
Recently, we observed threat actors leveraging bulletproof cloud instances to create their botnets. The cloud provides them scalability, agility, and ease of management. Given proper opsec while conducting attacks, there is less risk of their campaigns getting exposed.
By orchestrating only a few very capable bots (cloud instances) and leveraging widely available cloud orchestration tools, they can quickly and easily spin up stable attack infrastructures and move them when compromised.
By leveraging anonymous proxies, they can conceal their infrastructure and randomize their source IP to make detection more difficult. Bulletproof cloud providers do not act on abuse complaints. As such, malicious services hosted by bulletproof cloud providers are much harder to take down compared to traditional public cloud providers.
Another way to create an effective DDoS botnet is through crowdsourcing. NoName057(16) provides a malware binary that volunteers can download and run on their Windows desktop, Apple Mac mini or MacBook, Android mobile device, or even cloud instances they rent or own.
The bots owned and run by volunteers, like in traditional botnets, connect to a central command and control infrastructure to receive target lists and commands. NoName057(16) manages and operates the C2 infrastructure and publishes the client bot software on its Telegram group ‘DDoSia project’ for anyone to download.
They support their volunteers through email at the Protomail email ‘[email protected]’ or through their ‘DDoSia project’ Telegram group.
Using a Telegram bot ‘@DDosiabot,’ new volunteers can register and receive a unique ID. This ID is provided in a client_id.txt plain text file and needs to be copied in the same folder that the bot executes from.
The ID authorizes the bot to download attack target lists from the C2 infrastructure and upload attack statistics to the same C2 servers to track the number of attacks performed by the volunteer’s bot(s). The volunteer can run multiple instances of the bot in different locations; they all authenticate and register attacks through the same ID. By tracking the number of attacks, DDoSia can provide leaderboards and financial incentives for their most active volunteers.
NoName057(16) leverages Cryptobot to pay their volunteers in TON coin. @Cryptobot is a Telegram bot that provides a Telegram-based multicurrency wallet to store and trade cryptocurrencies.
The bot supports TON coins, a cryptocurrency initially launched by Telegram and called Telegram Open Network but then abandoned and taken over by the community and renamed to The Open Network.
Since a volunteer has registered and received a unique ID through @DDosiabot, the NoName057(16) operators can pay out through Cryptobot to the Telegram account that was used to register the DDoSia bot and received the ID. The ID is what connects the bot, the attacks, the telegram channel, and ultimately the payouts.
Q6. Given the changes in the remuneration system, how lucrative is it for a regular criminal volunteer participating in these attacks? Is there any data or estimation on the average payout for a participant compared to other similar operations?
The payouts a volunteer receives are based on the number of attacks performed by the volunteer versus the total number of attacks performed by all active volunteers on a particular day as well as the budget allocated by the NoName057(16) operators. There is no fixed amount in the new payout scheme.
Initially, when the DDoSia project was launched in October 2022, the payout scheme was fixed:
- 80,000 rubles for first place
- 50,000 rubles for second place
- 20,000 rubles for third place.
A budget of 50,000 rubles was shared between fourth and tenth place based on the volunteers’ attack ratios. Back then, payments were also done in Bitcoin. However, they never paid out.
Working undercover and simulating attacks, we reached NoName057(16)’s top 10 for several consecutive weeks. We were hoping to get a payment so we could track the Bitcoin wallet used for the payment, identify which wallets got paid, and learn where the money in the wallet originated from.
Alas, we were never paid for our simulated attacks. Only after NoName057(16) announced their new financial model on March 14, 2023, did we receive payouts for our efforts. However, this time, payouts were made in TON and through the Telegram Cryptobot.
We did not find a way to trace the origins of the payments, except that the TON payments were received from ‘NNMDDoSia #A91353’.

Since the payout depends on the total number of registered attacks per day, there is no fixed payout amount.
Some days the #1 spot earned 2 TON while other days it earned close to 20 TON. See below for a few examples of how this translates to earnings in USD.

To estimate how much a top 10 attacker could earn in a month, assuming that a top volunteer gets paid anywhere between 2 and 30 USD daily, the total monthly earnings would be between 60 and 900 USD.
To achieve a #1 spot, you would have to register between 1 million and 100 million attacks per day, which requires an infrastructure that is able to sustain between 10 and 1000 encrypted web requests per second.
The requests would need to be routed through an anonymizing VPN tunnel, which limits the throughput of a single attack node. More than 1,000 requests per second would require multiple nodes running bots in parallel. A single Windows gaming PC or MacBook Pro would not suffice.
NoName057(16) is a large network of operators who likely have members who are regularly trained and hired to work on the messages they post on Telegram and other mediums. They have adapted to changing payment options over the years and mean to make their presence in the underground world.
Radware threat researcher’s undercover activity unearthed very intricate operations of the NoName057(16) hacktivist group. Their threat to a journalist reflects how clearly they do not want to be associated with Killnet or other groups and do not seem to show signs of stopping sooner.