Why Businesses Must Upgrade to Quantum-Safe Encryption Before It’s Too Late
Cybersecurity has always had to keep pace with the evolution of cyberattacks. These attacks started gaining prominence in the late 80s, in line with the spread of internet access. Initially, viruses, worms and different types of malware were configured to target laptops and desktops. These attacks over time evolved into SQL injection, web-based and social engineering attacks. DDoS attacks followed, and so did Zero Day attacks. Cybersecurity evolved accordingly. Today, the emergence of AI has led to the development of next-gen security platforms. These platforms include Secure Access Service Edge (SASE), XDR and more.
The idea behind cybersecurity is to stay one step ahead of evolving cyberattacks. As the era of quantum computing dawns, it is necessary to be prepared. The Quantum Computing Cybersecurity Preparedness Act was passed in 2022. The focus of this Act is on federal agencies and asking them to prepare against quantum computing attacks. But it makes sense for businesses to be ready as well. 48% of organizations don’t have security readiness to address quantum computing threats.
Not a good place to be from a cybersecurity perspective.
Shor’s Algorithm
Why are cybersecurity professionals so scared of quantum threats? The reason traces back to the Shor Algorithm. In 1994, Peter Shor, an American theoretical computer scientist, discovered an algorithm. The purpose of this algorithm was to accelerate the factoring of large numbers.
This development was a problem.
Computers that are commonly used today are hard-pressed to factor huge numbers. This is why modern encryption systems work. Cybercriminals are unable to break down huge combinations into prime components. On the other hand, the Shor algorithm can do this easily, provided it does so on a quantum computer. This algorithm can break asymmetric encryptions that are popularly used today.
The lesson from the Shor algorithm is clear: start preparing today for quantum threats.
What are Quantum Threats
Today, we are using high-performance computer systems to get our work done. However, in technological terms, these are still ‘classical’ computers from a quantum perspective. The high-performance computing prevalent today will soon evolve into quantum computing. Such computation leverages the frameworks of quantum mechanics to solve complex problems. While classical computers use bits, quantum computing works with qubits. The framework leverages different quantum phenomena to work on multiple possibilities simultaneously.
Complex calculations, the backbone of encryption, can thus be solved quickly.
Why does quantum computing present a cyber risk?
Traditional or classical computers cannot process information quickly. But quantum computers can. This fact means existing encryption methods can be cracked easily. Your organization might pride itself on using robust encryption and following encryption best practices. But, enter quantum computing, and critical digital information won’t be safe anymore.
Here are some of the risks of quantum computing, or to be specific, quantum threats:
- Obsolescence of Public Encryption
Some of the common types of encryption we use today include RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Cryptography), and DH (Diffie-Hellman Key Exchange). The first two are asymmetric types of encryption. The third is a useful fillip to the first to establish secure communication, with secure key exchange. RSA relies on very large integers, and ECC, on very hard-to-solve math problems. As can be imagined, these cannot be solved with traditional computing. However, the time is not far when public-key encryption methods will be rendered obsolete via quantum computing.
- Harvest Today, Decrypt Later
Cybercriminals think long-term. They are well aware that quantum computing is still some time away. But that doesn’t stop them from stealing encrypted information. Why? They will store it securely until quantum computing becomes readily available; then they will decrypt it. The impending arrival of quantum computers has set the cat amongst the pigeons. Cybercriminals can’t wait to score a huge payday later, making concerted efforts today.
Blockchain is not unhackable, but it is difficult to hack. A bunch of cryptographic algorithms keep it secure. These include SHA-256 (Secure Hash Algorithm 256-bit) and ECDSA (Elliptic Curve Digital Signature Algorithm). Today, cybercriminals might not attempt to target blockchains and steal crypto. But tomorrow, with the availability of a quantum computer, the crypto vault can be broken into, without trouble.
- Wide Gap Between Cybersecurity Posture and Attacks
We keep saying that quantum computing and quantum computing-enabled threats are still some time away. And, this is true. But when the technology is here, it will evolve and gain traction. The attacks will also evolve accordingly. The raw computation power of quantum machines will ensure that encryption can be broken easily. Forging digital signatures, decrypting secure communication, or accessing and decrypting critical information will be a breeze. You therefore need to start upgrading your security systems to future-proof them. Otherwise, you will be caught in a vicious cycle of playing catch-up.
Understanding the Quantum Threat Timeline
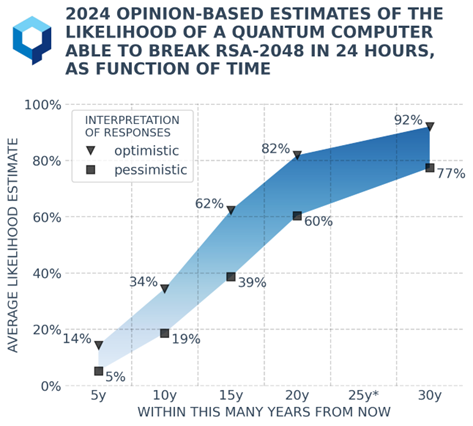
The above figure is from a Quantum Threat Timeline Report 2024, by Global Risk Institute. The report pins a timeline for when the Cryptographically Relevant Quantum Computer (CRQC) will be available for use. It brings together the views of global experts, whose most optimistic estimates suggest the CRQX availability will be between 5 and 30 years.
In this case, optimistic means there is still some time to set up a quantum-resistant infrastructure, but a cautious estimate suggests it can happen within a decade.
There are two critical aspects you must consider to plan for a post-quantum threat world.
Take a good, hard look at the data generated by your organization today. Will this data still be relevant or valuable for cybercriminals once the first quantum computer arrives in mainstream use? For example, banking information of a customer or just renewed credit card details (expiry in the next ten years) will be susceptible to quantum threats. This data can be stolen today and decrypted later.
Do you have plans to update or modify your existing hardware and software that manage and control data? Also, think about the in-development systems and products that will go live. Many of these might become operational when quantum computers are due to arrive on the scene. The fact that these systems and software will be updated over the years means they will be at risk of quantum threats.
Key stakeholders must come together to understand and evaluate the sensitive nature of the data and the systems that process, assess, share, and control this data. Figure out the level of susceptibility these have to quantum threats and devise a remediation plan accordingly.
Why Traditional Encryption Won’t Survive?
A recent Google study reported that breaking 2048-bit RSA encryption might only take a week of computation on a quantum machine with 1 million noisy qubits. A slowly dawning reality is that the shift from traditional asymmetric encryption to quantum-resistant encryption must happen now.
Before quantum computing was on the horizon, asymmetric encryption was considered perfectly safe and configured to protect critical data. Existing computing cannot easily factor significantly larger prime numbers that underpin this type of encryption. This is a computationally intensive exercise. It is both time and cost-prohibitive and therefore non-viable.
Quantum computing breaks this non-viability barrier.
The amount of information that quantum computers can store and process is far larger than traditional computers. This means their computational capacity is also significantly faster, enabling them to break asymmetric encryption easily.
We are not far from a scenario wherein a cybercriminal with access to a quantum computer running Shor’s algorithm, decrypts RSA and ECC encryption, exposing any private key they guard. This will have repercussions on the everyday security layers that we take for granted and which are delivering immense security value to date. These include SSL/TLS for web sessions, VPN handshakes, PGP and S/MIME email signatures, OS and app code-signing, and even blockchain wallets or smart contracts.
Until those systems migrate to post-quantum algorithms, they may become redundant soon.
What is Post Quantum Cryptography
Simply put, post-quantum cryptography helps you address the threats posed by quantum computing. You don’t have to worry about Shor’s algorithm in conjunction with a quantum computer breaking traditional encryption algorithms. Your quantum-resistant algorithm will keep this threat at bay.
The three categories of quantum-risk resistant solutions include:
- Post-Quantum Cryptography: These are new math-based public-key quantum-resistant algorithms.
- Quantum Key Distribution: This framework is supported by quantum physics for secure communication channels that share symmetric cryptography keys.
- Quantum Random Number Generation: This framework fuels randomness for building robust security protocols.
NIST, or the National Institute of Standards and Technology (NIST), has already come out with a list of post-quantum cryptographic standards primarily covering key exchange and digital signatures. This includes Federal Information Processing Standards (FIPS):
- FIPS 203: This standard, based on ML-KEM (Module-Lattice-Based Key-Encapsulation Mechanism), focuses on general encryption, and is underpinned by small encryption keys that can be shared easily by two parties
- FIPS 204: This standard, based on ML-DSA (Module-Lattice-Based Digital Signature Algorithm), focuses on protecting digital signatures.
- FIPS 205: This standard based on SLH-DSA (Stateless Hash-Based Digital Signature Algorithm), also focuses on digital signatures; the difference being the math approach. If ML-DSA is broken into, this algorithm is the backup.
What does a Quantum Threat Cybersecurity Roadmap look like?
CISOs must start the process to achieve a post-quantum cybersecurity posture today. While different threat timelines offer different estimates, there is no doubt that quantum threats are real and about to arrive.
Here’s a roadmap you can use to achieve readiness:
- Build a Business Case
Make sure you start with preparing a list of tangible impacts to your business with the emergence of post-quantum threats. Also, calculate the ROI of implementing a proactive plan of action before the threats reach your organization’s door.
- Evaluate and Analyze the Threat Perception
Make sure you first understand the at-risk data and processes with respect to quantum computing. This will help you zero in on the post-quantum cryptographic systems that will address a rapidly evolving threat landscape.
- Asset Prioritization
Create an inventory of the various security protocols used in your organization, including encryption frameworks. Also, create a list of assets that you feel are most susceptible to post-quantum threats.
- NIST Standards
NIST has already released the list of recommended post-quantum cryptographic standards. Understand these and check how you can begin the implementation process.
- Begin the Quantum-Safe Journey
Every journey begins with small steps. Methodically start transitioning to a quantum-safe cybersecurity posture. Update your software and hardware, and modify legacy systems. Also, have replacement timelines for systems in place.
- Continuous Risk Assessment
Your roadmap will evolve as the years go by. New information on post-quantum threats and new solutions will be available. Keep evaluating existing high-risk areas, security protocols, and make incremental improvements.
Final Thoughts
The battle against cyberthreats is won or lost based on your proactive approach (or the lack of it). We are well aware of how organizations dropped the ball on security and experienced an expensive data breach. Do not be that organization. Start taking action and start moving towards post-quantum cryptography to keep your data safe.
About the Author
 Ann-Anica Christian is the content strategist and creator of the SSL2BUY.
Ann-Anica Christian is the content strategist and creator of the SSL2BUY.
Ann-Anica Christian is an accomplished content strategist and creator with more than seven years of expertise in SaaS, digital eCommerce, and cybersecurity. Her work has been featured on SSL2BUY Cybersecurity sections, serving as a trusted resource for developers, IT professionals, and business owners. Since beginning her career in technical content development, she has built a reputation for translating complex concepts in website security, IoT, SSL/TLS encryption, and public key infrastructure (PKI) into clear, actionable insights for diverse audiences.
In her current role, Ann-Anica leads content strategies that combine technical depth with business objectives, delivering clarity, accuracy, and engagement across publications. She also authors journals highlighting advancements in technology sectors, reflecting her deep understanding of evolving security threats and best practices, and enabling readers to navigate the fast-changing cybersecurity landscape with confidence.
Connect with Ann-Anica at [email protected] or company website http://www.ssl2buy.com/ to learn more about her work.