The EU threat landscape is dominated by hacktivism, DDoS attacks and ransomware, according to the new 2025 ENISA Threat Landscape report.
ENISA, the EU Agency for Cybersecurity, released the report today. It examines nearly 4,900 cyberattacks that occurred between July 2024 and June 2025 and offers insights into the broad cyber trends affecting the continent.
Key findings include:
- DDoS attacks – largely launched by hacktivists – were by far the most common cyber incident, accounting for just under 77% of reported incidents. Intrusions were a distant second at just under 18%.
- Supply chain attacks are on the rise, and the lines between hacktivism, cybercrime and state-sponsored threats continue to blur, with “increasingly shared toolsets and modus operandi.”
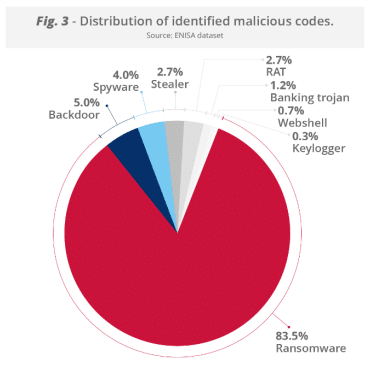
- Ransomware was by far the most dominant malware type, accounting for 83.5% of all malware identified in intrusions. Backdoors, spyware, infostealers, RATs, banking trojans, webshells and keyloggers all accounted for 5% or less (chart below).

“The reporting period highlights a maturing threat environment characterised by rapid exploitation of vulnerabilities and growing complexity in tracking adversaries,” the report said. “Intrusion activity remains significant, with ransomware at its core.”
Phishing, Vulnerability Exploits and Mobile Threats Dominate EU Threat Landscape
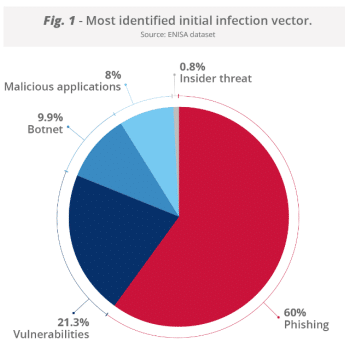
Phishing was the most common initial intrusion vector at 60%, well ahead of vulnerability exploitation at 21.3%. Botnets and malicious applications were at 9.9% and 8%, and insider threats at just under 1% (chart below).

Vulnerability exploits are much more likely than phishing to result in malware deployment, by 68% to 23%.
“Overall, the distribution underscores that while phishing dominates the threat landscape, technical exploits, malware delivery mechanisms and insider risks remain meaningful concerns,” the report said.
Artificial intelligence (AI) “has become a defining element of the threat landscape,” accounting for more than 80 percent of worldwide social engineering activity, with jailbroken models, synthetic media and model poisoning techniques being used to enhance threat actor effectiveness.
ClickFix-style scams and the weaponization of compromised WordPress sites to distribute infostealers are other growing threat trends.
Of recorded intrusions, 68.6% led to data breaches that were offered for sale on cybercrime forums, and 2.8% of those advertised breaches were presented as a direct outcome of a ransomware attack. Data exfiltration, including credential theft (8.9%) and strategic data collection (21.3%), accounted for 30.2% of intrusion outcomes, and fraud was an outcome in 1.2% of cases.
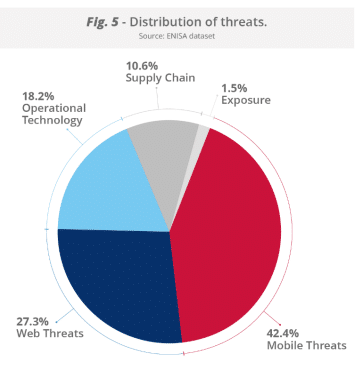
Mobile threats account for the largest share of threats at 42.4%, followed by web threats at 27.3% (chart below). Operational technology (OT) threats represent 18.2% of threats and supply chain risks comprise 10.6% of threats, “showing that attackers are actively leveraging indirect pathways through third-party providers and dependencies.”

Hacktivism, Cyberespionage and Cybercriminals in the EU
State-aligned threat groups “intensified their long-term cyberespionage campaigns against the telecommunications, logistics networks and manufacturing sectors in the EU, demonstrating advanced tradecraft such as supply chain compromise, stealthy malware frameworks and abuse of signed drivers,” the report said.
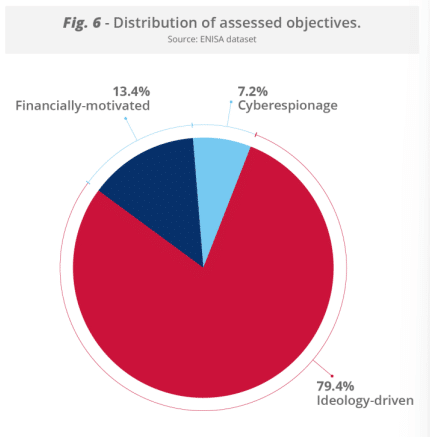
While hacktivist activity – much of it aligned with Russia – continues to dominate the EU threat landscape, accounting for nearly 80% of recorded incidents, it is “driven primarily by low-level distributed denial-of-service operations.” While only 2% of hacktivism incidents result in service disruption, “these campaigns demonstrate how low-cost tools are scaled for ideology-driven operations,” ENISA said.
In terms of sectoral targeting, public administration networks remain a primary focus of attacks at 38%, notably for hacktivists and state-sponsored threat actors. Transportation has emerged as a high-value sector, particularly maritime and logistics. Aviation and freight operations have been the target of ransomware attacks, while “digital infrastructure and services remain strategic targets for both cyberespionage and ransomware operators,” ENISA said.
Cybercriminals, meanwhile, have “notably responded to the actions of law enforcement by decentralising operations, adopting aggressive extortion tactics and capitalising on regulatory compliance fears.”
Below is a breakdown of EU cyberattacks by motivation, with ideologically-driven attacks far outpacing financially-motivated attacks and cyberespionage.