Akira ransomware group added U.S.-based software company Parathon to its victim list. The hackers claimed to have 560 GB of data of employee data and other information, exfiltrated after the Parathon cyber attack.
Parathon cyber attack
Threat Intelligence Service Falcon Feeds tweeted about the Parathon cyber attack with the above screenshot. The screenshot is from the dark web portal of the Akira ransomware group naming Parathon as its latest victim.
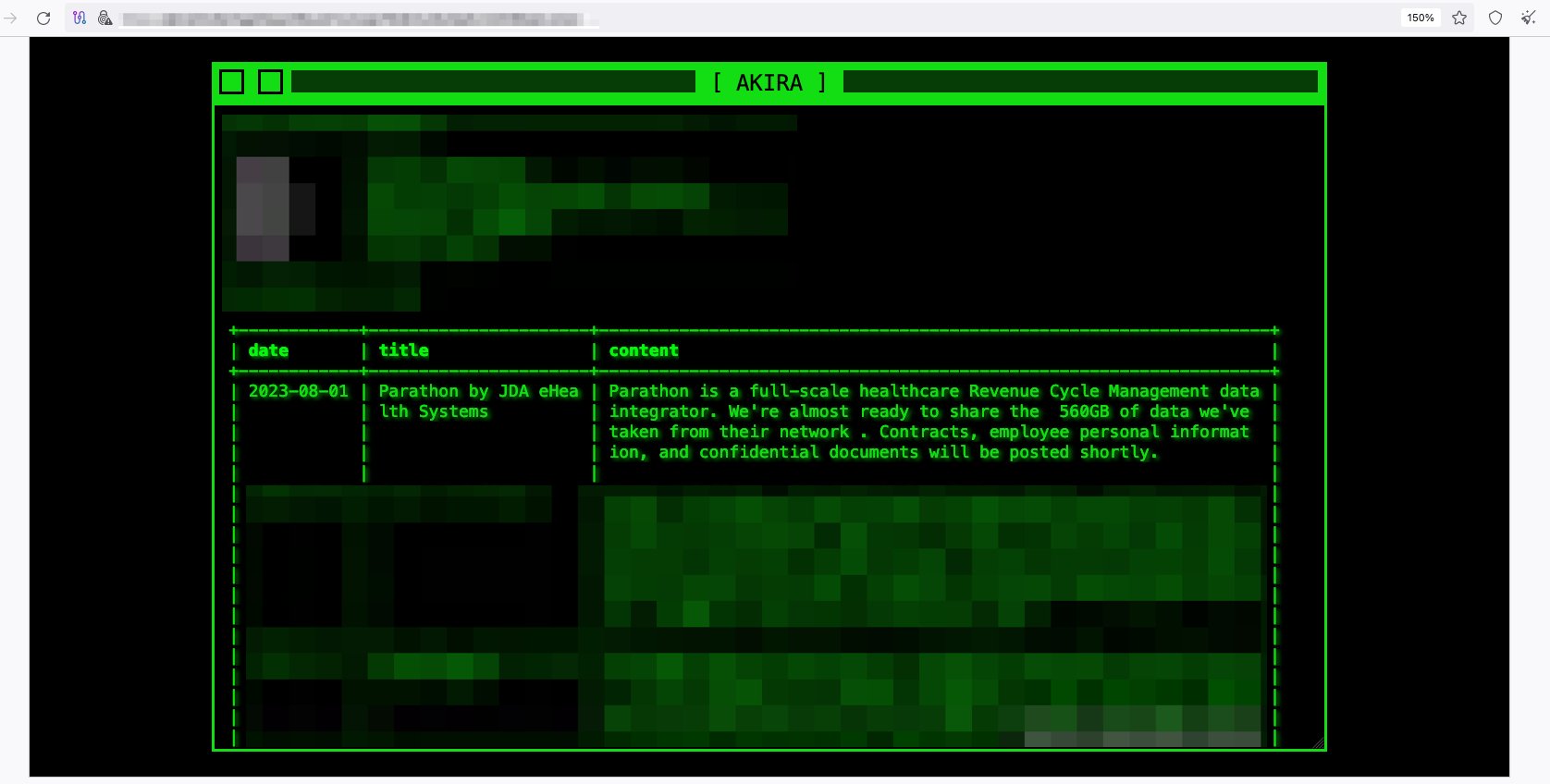
“Parathon is a full-scale healthcare revenue cycle management data integrator,” wrote hackers from Akira on their website. “We’re almost ready to share the 560GB of data we’ve taken from their network,” the dark web post added.
The hackers claimed to have exfiltrated contracts, employee personal information, and confidential documents from the Parathon cyber attack. Akira hackers also threatened to release the confidential stolen data shortly.

The Cyber Express emailed Parathon which provides healthcare technology solutions for revenue cycle management for comments about the alleged Parathon cyber attack. We will update this report based on their reply.
The alleged Parathon cyber attack and Akira ransomware group
In a span of nearly five months since March 2023, the Akira ransomware group targeted over 63 organizations. They mostly targeted small to medium-sized businesses (SMBs). The group was discovered in March 2023.
The hackers from the group have been known to offer targeted companies choose what they would like to pay.
Companies can choose to pay just for decryption and skip paying for the deletion of data or vice versa. Akira’s ransom demands range between $200,000 and $4,000,000. Moreover, they claim to not cause severe financial loss to the targeted organizations.
So they charge a ransom that the victims can pay based on their income and savings.
The hackers were found often targeting organizations in the United States of America and Canada. They state that they will release the data within 24 hours of receiving the ransom.
Hackers from the Conti ransomware group have been linked to the Akira ransomware group. A pro-Ukrainian member of the group allegedly leaked the Conti ransomware group’s source. Conti and Akira both ignore the same file types and directories. They both share similar encryption algorithms.
Akira targets Windows and Linux systems. They have been known to exploit systems that lack multi-factor authentication.
They also gain unauthorized access by exploiting stolen credentials released on the dark web. The malware used by Akira members deletes backup folders so the victims cannot restore the data.
Akira ransomware, now in Linux too
Cyble Research and Intelligence Labs (CRIL) in June uncovered a new and advanced Linux variant of the Akira ransomware, signaling a change in tactics by the notorious ransomware group.
This development raises concerns about the growing vulnerability of Linux environments to cyber threats.
The Akira ransomware group has been actively targeting various organizations across multiple sectors, posing a significant threat to their cybersecurity and sensitive data.
Since its emergence in April 2023, the Akira ransomware has already attacked 46 publicly disclosed victims, and an additional 30 victims have been identified since CRIL’s previous report, indicating the group’s expanding reach, with the majority of victims based in the United States.
The Linux variant of Akira ransomware is distributed in the form of a 64-bit Linux Executable and Linkable Format (ELF) file.
To execute this malicious file, specific parameters must be provided, including the paths of files/folders to be encrypted, the shared network drive to be encrypted, the percentage of files to be encrypted, and the creation of a child process for encryption.
When the Linux variant of Akira ransomware is executed with the correct parameters, it uses a special encryption method called RSA to lock the victim’s files, rendering them unreadable without the decryption key.
The ransomware specifically targets certain file types, such as documents, databases, images, and more, encrypting any matching files it finds.
The encryption process involves employing various symmetric key algorithms, including AES, CAMELLIA, IDEA-CB, and DES, to scramble the data in the targeted files, making them inaccessible to the victim.
Once encrypted, the ransomware appends the “.akira” file extension to each compromised file, allowing for easy identification of the encrypted files.
After encrypting the victim’s data, the Akira ransomware displays a ransom note, demanding payment for the decryption key.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.