Etiket: Vulnerabilities
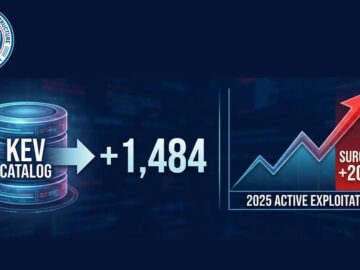
The United States Cybersecurity and Infrastructure Security Agency (CISA) has significantly expanded its Known Exploited Vulnerabilities (KEV) Catalog to 1,484…
SECURITY | AI | PURPOSEUNSUPERVISED LEARNING is a newsletter about upgrading to thrive in a world full of AI. It’s…
CVE-2025-62554 Microsoft Office Remote Code Execution Vulnerability Critical Remote Code Execution Access of resource using incompatible type (‘type confusion’) in…
Before JSON Web Tokens (JWTs) became popular in today’s app development landscape, web applications predominantly used server-side sessions, which presented…
Security researchers from Kaspersky have detailed a sophisticated exploit chain dubbed “ToolShell,” actively targeting on-premise Microsoft SharePoint servers worldwide. The…
Microsoft has released its June 2025 Patch Tuesday security updates, addressing a total of 66 vulnerabilities across its software ecosystem….
CVE Number (Link) CVE Title Impact Max Severity CVE-2025-26663 Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability Remote…
Welcome to this week’s Cybersecurity Newsletter, providing you with the latest updates and essential insights from the rapidly evolving field…
Welcome to this week’s Cybersecurity Newsletter, which presents the latest updates and key insights from the continuously evolving domain of…
Welcome to this week’s Cybersecurity Newsletter, where we explore the most recent developments and essential updates in the world of…
The weekly cyber security newsletter is a brief summary of what the most recent threats, vulnerabilities, and innovations in the digital security…
Penetration testing is vital as it helps identify vulnerabilities in a system or network, allowing organizations to proactively strengthen their…