Etiket: Trojans
Mitiga researchers have documented a new post-exploitation technique attackers can use to gain persistent remote access to AWS Elastic Compute…
Share: Share this on X : Attackers can turn AWS SSM agents into remote access trojans Share this on Facebook : Attackers can turn AWS SSM agents into remote access trojans Share this on Pinterest : Attackers can turn AWS SSM agents into remote access trojans Share this on Linkedin : Attackers can turn AWS SSM agents into remote access trojans
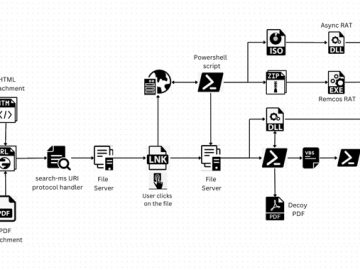
Jul 28, 2023THNMalware / Cyber Threat A legitimate Windows search feature is being exploited by malicious actors to download arbitrary…
Share: Share this on X : Hackers Abusing Windows Search Feature to Install Remote Access Trojans Share this on Facebook : Hackers Abusing Windows Search Feature to Install Remote Access Trojans Share this on Pinterest : Hackers Abusing Windows Search Feature to Install Remote Access Trojans Share this on Linkedin : Hackers Abusing Windows Search Feature to Install Remote Access Trojans