Etiket: Threat
In the era of digital transformation, where data flows across borders and devices, data security is paramount. Cyberattacks are no…
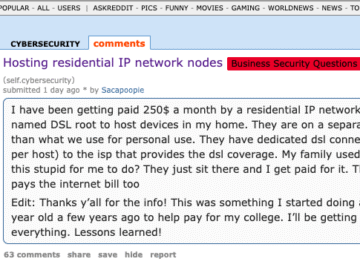
The cybersecurity community on Reddit responded in disbelief this month when a self-described Air National Guard member with top secret…
Why Businesses Must Upgrade to Quantum-Safe Encryption Before It’s Too Late Cybersecurity has always had to keep pace with the…
In today’s digital-first world, cybersecurity is more critical than ever. As cybercriminals continue to evolve their tactics, individuals, businesses, and…
Appdome, Appdome’un ThreatScope Mobile XDR’sinde Threat Dynamics adlı yeni bir AI-Native tehdit yönetimi modülünün sunulacağını duyurdu. Threat Dynamics, 400’den fazla…
Next-Generation Technologies & Secure Development , Threat Intelligence Acquisitions, AI and Emerging Threats Define Strategy for Recorded Future, Google Michael…
You can tell the story of the current state of stolen credential-based attacks in three numbers: Stolen credentials were the…
Dünyanın dört bir yanındaki kuruluşlar, yaygın siber saldırılar nedeniyle uzun süreli kesinti süreleri ve gelir kaybıyla mücadele ederken Rubrik, Rubrik…
Netwrix, Netwrix Threat Manager’ın yeni bir sürümünü yayınladı. Yükseltme, ürünün yeteneklerini şirket içi Active Directory (AD) örneklerine ek olarak Microsoft…
Yeni Nesil Teknolojiler ve Güvenli Geliştirme, Tehdit Avı, Tehdit İstihbaratı Anlaşma Mastercard’ın Dijital İşlemler İçin Daha Fazla Koruma ve Güven…
Palo Alto Networks’ün siber tehdit kolu ‘Unit 42’ tarafından yapılan bir araştırmaya göre, Rus İstihbaratı’na ait olduğu iddia edilen APT28,…
Geleceğe hazır saldırı korumasında lider olan Cybereason, bugün Zimperium tarafından desteklenen Cybereason Mobil Tehdit Savunmasının kullanıma sunulduğunu duyurdu. Bu, mobil…