Etiket: Malware
The list of LOLBAS files – legitimate binaries and scripts present in Windows that can be abused for malicious purposes,…
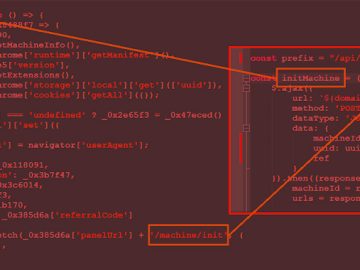
Aug 03, 2023THNBrowser Security / Malware Cybersecurity researchers have discovered a new version of malware called Rilide that targets Chromium-based…
The malicious Rilide Stealer Chrome browser extension has returned in new campaigns targeting crypto users and enterprise employees to steal…
Governance & Risk Management , Operational Technology (OT) Kaspersky Identifies Campign From Beijing-aligned APT31 Threat Actor Prajeet Nair (@prajeetspeaks) •…
Researchers have discovered a new post-exploitation technique in Amazon Web Services (AWS) that allows hackers to use the platform’s System…
According to reports, a new Android malware is circulating under the guise of a fake chat application that is being…
The Italian organizations, including tax agencies, were targeted by a new malware downloader delivering banking Trojan. The new loader malware…
Chinese state-sponsored hackers have been targeting industrial organizations with new malware that can steal data from air-gapped systems. Air-gapped systems…
The developer behind the FraudGPT malicious chatbot is readying even more sophisticated adversarial tools based on generative AI and Google’s…
IN SUMMARY Cybersecurity researchers at Kaspersky Labs identified the malware. The malware used by APT31 targets European industrial control systems….
Recently discovered data-stealing malware is targeting macOS users with a sneaky approach that uses Hidden Virtual Network Computing (hVNC). It’s…
In the wake of WormGPT, a ChatGPT clone trained on malware-focused data, a new generative artificial intelligence hacking tool called…