Etiket: guide
Endpoint management and security is not one of the top areas of discussion regarding IT security, and this doesn’t come…
Share: Share this on X : What is Endpoint Management ? -A Detailed Security Guide Share this on Facebook : What is Endpoint Management ? -A Detailed Security Guide Share this on Pinterest : What is Endpoint Management ? -A Detailed Security Guide Share this on Linkedin : What is Endpoint Management ? -A Detailed Security Guide
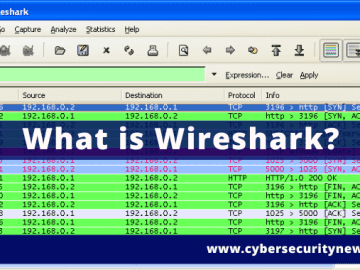
Wireshark’s capabilities to analyze and monitor network traffic make it an indispensable tool for security professionals, network administrators, and even…
Share: Share this on X : What Is Wireshark ? – A Detailed Network Analysis Guide Share this on Facebook : What Is Wireshark ? – A Detailed Network Analysis Guide Share this on Pinterest : What Is Wireshark ? – A Detailed Network Analysis Guide Share this on Linkedin : What Is Wireshark ? – A Detailed Network Analysis Guide
Whatever assets you happen to control, you want to be sure that they’re secure. Even if your system is lucky…
Share: Share this on X : A Simple Guide to Vulnerability Triage: A Structured Approach to Vulnerability Management Share this on Facebook : A Simple Guide to Vulnerability Triage: A Structured Approach to Vulnerability Management Share this on Pinterest : A Simple Guide to Vulnerability Triage: A Structured Approach to Vulnerability Management Share this on Linkedin : A Simple Guide to Vulnerability Triage: A Structured Approach to Vulnerability Management
Contemporary organizations understand the importance of data and its impact on improving interactions with customers, offering quality products or services,…
Share: Share this on X : How GRC protects the value of organizations — A simple guide to data quality and integrity Share this on Facebook : How GRC protects the value of organizations — A simple guide to data quality and integrity Share this on Pinterest : How GRC protects the value of organizations — A simple guide to data quality and integrity Share this on Linkedin : How GRC protects the value of organizations — A simple guide to data quality and integrity