Etiket: Flaw
Fraud Management & Cybercrime , Governance & Risk Management , Patch Management Also: npm Packages Infiltrated, FBI Issues Fraud Alert,…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Adopting a counterintelligence mindset in…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Can your earbuds recognize you?…
01 Ekim 2025Ravie LakshmananAI Güvenliği / Bulut Güvenliği Red Hat OpenShift AI hizmetinde, saldırganların ayrıcalıkları artırmasına ve belirli koşullar altında…
OnePlus’tan Android tabanlı işletim sistemi olan OxyGenos’un birden çok sürümünde bir güvenlik açığı, yüklü herhangi bir uygulamanın izin veya kullanıcı…
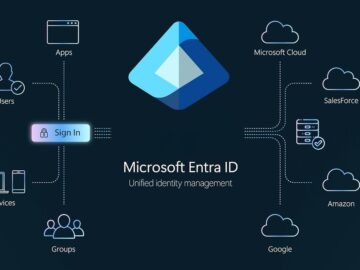
Legacy bileşenlerinin eleştirel bir kombinasyonu, dünyadaki her şirketin Microsoft Entra Kimlik Kiracısına tam erişim sağlayabilir. Ölümcül karışım, “aktör jetonları” olarak…
Bulut kırılganlığı açıklamadan önce sabitlenirken, bunu keşfeden araştırmacı, güvenlik topluluğunda bazı endişe duyan felaket saldırılarına yol açabileceğini söylüyor. Source link
Araştırmacılar, ChatGPT’nin derin araştırma temsilcisinde, saldırganların herhangi bir kullanıcı etkileşimi olmadan sessizce hassas Gmail verilerini çalmasına izin veren kritik bir…
Kubernetes C# istemci kütüphanesinde yakın zamanda açıklanan bir güvenlik açığı, saldırganların API sunucusuna karşı ortada insan (MITM) saldırıları yapmasına izin…
Milyonlarca insan ve işletme, sözleşmeler, raporlar, fotoğraflar ve araştırma makaleleri gibi önemli dosyaları saklamak için her gün Google Drive’a güveniyor….
Kubernetes Gitops dağıtımları için kullanılan popüler bir açık kaynaklı araç olan Argo CD’de büyük bir güvenlik kusuru keşfedildi. Güvenlik açığı,…
Yaygın bir hizmet kesintisi şu anda dünyanın dört bir yanındaki Microsoft Teams kullanıcılarını etkiliyor ve işbirliği platformundaki gömülü ofis belgelerine…