Etiket: Attackers
En azından Aralık ayından bu yana, Gelişmiş Kalıcı Tehdit (APT) Grubu, Rusya’daki kuruluşlara ait sistemlerde veri çalmak, algılama ve kriptominleri…
Krispy Kreme, the iconic doughnut chain, has become the latest victim of a cyberattack that has disrupted its online ordering…
Attackers are increasingly turning to session hijacking to get around widespread MFA adoption. The data supports this, as: 147,000 token…
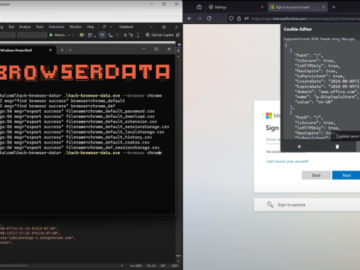
Attackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are)…
Mitiga researchers have documented a new post-exploitation technique attackers can use to gain persistent remote access to AWS Elastic Compute…
QNAP operating systems are robust, user-friendly software platforms that power NAS and NVR devices. QNAP offers four operating systems, and…
CISA has released three reports based on the analysis of backdoors planted on compromised Barracuda ESG appliances The Cybersecurity and…
The website of Israel’s largest oil refinery is inaccessible after it was attacked by an Iranian hacktivist group called Cyber…
Another actively exploited zero-day vulnerability (CVE-2023-35081) affecting Ivanti Endpoint Manager Mobile (EPMM) has been identified and fixed. The first zero-day…
Trust Wallet made a significant announcement on November 14th, 2022, unveiling its newly launched browser extension for wide usage. The…
Recent reports indicate that Metabase has been discovered with an unauthenticated Remote Code Execution (RCE) vulnerability that lets threat actors…
OpenAI’s ChatGPT, released in November 2022, stunned users with its diverse capabilities, answering questions and crafting custom essays, sparking widespread…