Etiket: Attacker
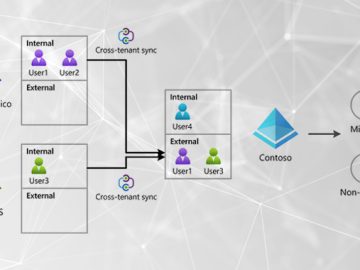
Aug 10, 2023The Hacker NewsThreat Detection / Attack Signal Attackers continue to target Microsoft identities to gain access to connected…
Share: Share this on X : Emerging Attacker Exploit: Microsoft Cross-Tenant Synchronization Share this on Facebook : Emerging Attacker Exploit: Microsoft Cross-Tenant Synchronization Share this on Pinterest : Emerging Attacker Exploit: Microsoft Cross-Tenant Synchronization Share this on Linkedin : Emerging Attacker Exploit: Microsoft Cross-Tenant Synchronization
The build and shared components on the CPUs are exploited by a method called Collide+Power. This attack vector does not…
Share: Share this on X : New Collide+Power Exploit Let Attacker Steal Sensitive Data Share this on Facebook : New Collide+Power Exploit Let Attacker Steal Sensitive Data Share this on Pinterest : New Collide+Power Exploit Let Attacker Steal Sensitive Data Share this on Linkedin : New Collide+Power Exploit Let Attacker Steal Sensitive Data
An Open-redirect vulnerability was discovered by IBM, which could allow threat actors to spoof the original URL of IBM Security…
Share: Share this on X : IBM Security Verify Access Let Attacker conduct phishing attacks Share this on Facebook : IBM Security Verify Access Let Attacker conduct phishing attacks Share this on Pinterest : IBM Security Verify Access Let Attacker conduct phishing attacks Share this on Linkedin : IBM Security Verify Access Let Attacker conduct phishing attacks