Etiket: Attack
How To Use This Report Enhance situational awareness of techniques used by threat actors Identify potential attacks targeting your industry…
Gather Data Sampling (GDS), belirli Intel CPU’ları etkileyerek saldırganların toplama yönergelerini kötü amaçlı kullanarak eski verileri çıkarmasına olanak tanır. Tüm…
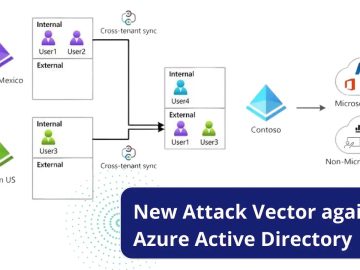
Gelen haberlere göre, SolarWinds saldırılarından sorumlu olan ve “Nobelium” olarak bilinen tehdit grubunun, Microsoft tarafından kullanıma sunulan yeni Kiracılar Arası…
TEL AVIV, Israel, Aug. 3, 2023 /PRNewswire/ — Vulcan Cyber, developers of the cyber risk management platform for all attack surfaces, today announced…
An unreported phishing campaign that disseminated a Python version of the NodeStealer has been found. NodeStealer gave threat actors the ability…
Aug 03, 2023THNVulnerability / Cyber Threat Hundreds of Citrix NetScaler ADC and Gateway servers have been breached by malicious actors…
Ever imagined a small online device capable of hacking into power grid control systems? Well, cybercriminals are already exploiting the…
Anonymous Sudan has claimed responsibility for a cyber attack on the website of a Nigerian mobile telecommunication company, MTN, on…
IN SUMMARY: Midnight Blizzard (aka NOBELIUM) was also involved in the SolarWinds hack. The group used hacked Microsoft 365 tenants…
The BlackCat ransomware group left a message on its dark web portal, claiming responsibility for the Tempur Sealy cyber attack….
In a recent incident involving a Microsoft Teams cyber attack, the tech giant has attributed the malicious campaign to a…
Customers of American retailer Hot Topic are being notified about multiple “credential-stuffing” cyberattacks that resulted in cracked accounts and sensitive information…